Demystifying Decentralized Identity Part 1
2019-12-03
Author: Riley Shu
Decentralized identity is one of the most popular concepts born out of the blockchain hype. The problem is that most people don’t really understand what it actually is and as more and more people join the discussion, the complexity of this concept increases exponentially.
In this article, and our upcoming posts in the next few weeks, our goal is to help everyone understand what decentralized identity is, why we need it, and how it actually works.
Before we dive into all the boring details that have probably confused you a thousand times, we need to understand why we need decentralized identities, and how decentralized identity represents a shift in thinking of how a user exists in the internet age. It sounds like something revolutionary, but in reality it is something that was born out of the early days of the internet, has come back into the forefront through the increased adoption of blockchain technologies and is quite simple to use. Let’s take a look at how we got to where we are.
Centralized Identity
Once upon a time, each time you sign-in to a website, you have to create an account.

In most cases the username we wanted was already taken.

And sometimes the password requirement varies making it difficult to find one that we can actually remember.
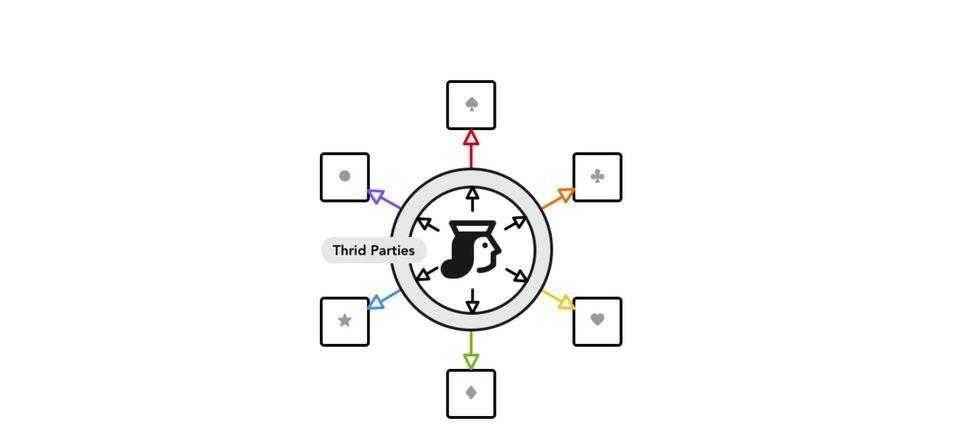
Third-Party Centralized Identity
So you end up having a bunch of different accounts and data silos spread out across the internet, which can lead to a countless number of password reset emails and is actually pretty annoying from an experience standpoint.
Then came the first solution that greatly improved the end-user experience. Some company says, “Hey. Why don’t you just use your account with us to log into other websites and we will do all the hard work for you?”
“This sounds doable.” You thought.
Like many people today, you are now logging in with your Facebook or Google account every time a new website asks a sign-up. It’s nice that you only need to remember one set of username and password, but that means those third parties have access to all the websites you have logged in and they can even connect your “digital exhaust” and dig out far more information about your activities than you can imagine. Most importantly, the third-party now has complete control over your digital identity. Are you able to reclaim that data anytime you want? Do you have any control at all over anything managed by the third party? Well, the long and short answer is no.
Is there a better solution? Why can’t you use the same set of usernames and passwords, but without the need of any third parties?
Decentralized Identity
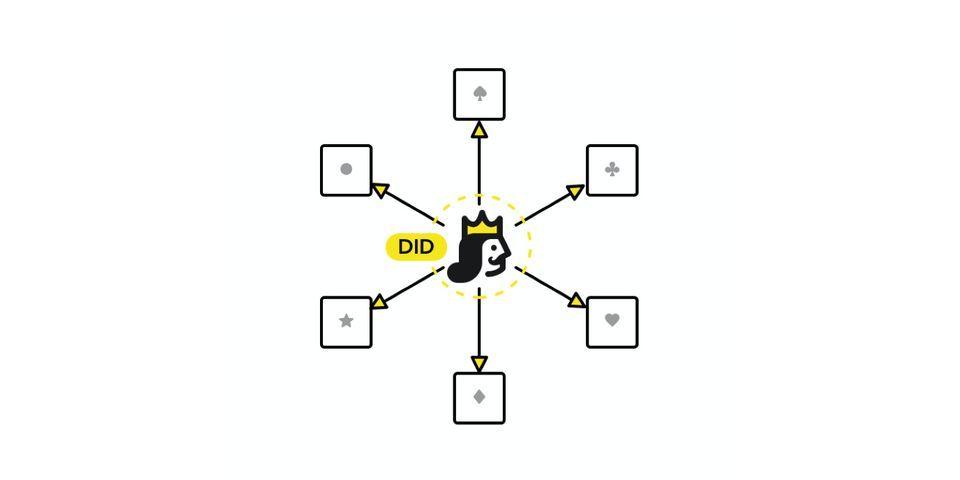
This is where a decentralized identity comes into the picture. Normally, you need a third-party to verify that the username and password do belong to you. The magic of decentralized identity is that it allows you to perform the verification yourself.
DID
You have probably seen DID and decentralized identity used in many places. There’s actually a tiny difference between the two. DID is short for decentralized identifier, which is a specific kind of decentralized identity proposed by W3C . While DID has clear definitions and requirements, decentralized identity is a higher level name for all the identifiers that are decentralized.
What is a decentralized identity? Decentralized identity actually consists of two parts: address and secret key.
The Address and Secret Key
The address is similar to username, while the secret key is similar to a password. The only difference is that with DID, the address is calculated from the secret key using cryptography. The only thing we need to know about this cryptography is that it helps us prove the ownership of a secret key of a DID.
No matter how hard it might sound, decentralized identity is just another kind of identity. Just like how we can identify people with their DNA, fingerprints or passport number, we know from our previous explanation that DID is an identifier consisting of a series of numbers and letters that helps us to differentiate different things, enabling anything to have their own “fingerprint”.
Anything Can Have a DID
Anything? Yes. As long as you can describe something as data, you can label this data with a DID. From certificates, licenses, to movie tickets, groceries, anything has a DID. What’s more, even relationships can have DID. For example, you can label your ownership of a car or your friendship with others.
If we can give anything an identity, will identities run out?
Mathematically, no. The reason is simple — there are too many addresses you can have! If you have 1,000,000,000 friends and each generates 1,000,000,000 addresses per second, it will take longer than the universe's life to get two same addresses.
How Decentralized Identity Works
Here’s let’s go through the whole process if using decentralized identity. If Alice wants to prove she’s the owner of the DID alicedid, she completes some calculation with her secret key, then presents the result, which is also called signature, to the public. Now people can perform a test using the signature and alicedid’s address to tell if Alice really holds that secret key. If Alice’s secret key is the right one, this test will pass. This means, unless Alice steals the secret key from the real owner, she’s the owner of this DID.
Confused? That’s okay. You just need to remember that decentralized identity can provide a unique “fingerprint” for everything; and owning a decentralized identity means having the secret key to that address. We will post another article in a week and you can continue learning more about Decentralized Identifiers and how they work here.